Questões de Concurso
Para tj-sc
Foram encontradas 1.760 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Assinale a alternativa que indica o que acontece quando se tenta compilar e executar a seguinte classe em Java:
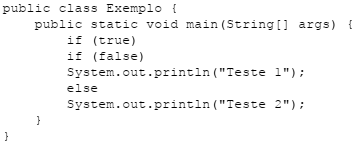
Considere o seguinte programa em Java:
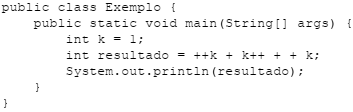
Ao ser executado, esse programa exibe o valor de “resultado”, que é:
Com relação à linguagem Java, analise as afirmativas a seguir e assinale a alternativa correta:
I. Java diferencia letras maiúsculas de minúsculas. Assim, por exemplo, “soma” e “SOMA” se referem a identificadores diferentes.
II. “main” é uma palavra reservada da linguagem Java.
III. Um objeto é uma instância de uma classe.
IV. String, real, integer e boolean são exemplos de tipos de dados primitivos (nativos) em Java.
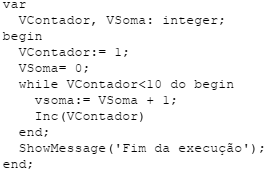
Considere o seguinte algoritmo:

Na implementação desse algoritmo em Delphi, a instrução “se numero = limite então” pode
ser escrita como:
Considere o seguinte trecho de código em Delphi e assinale a alternativa correta:
Considere o seguinte trecho de código em Delphi:
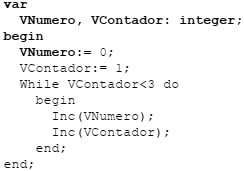
Ao final da execução desse trecho de programa, a variável VNumero possui o valor:
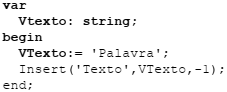
Ao final da execução desse trecho de programa, a variável VTexto possui o valor:
I. “Projetos” são atividades contínuas e repetitivas, sem data de término definida.
II. “Programas” são grupos de projetos relacionados entre si que são administrados de modo coordenado.
III. Uma das competências necessárias a um bom gerente de projetos é a habilidade para resolução de conflitos.
IV. Para determinar se um projeto foi bem-sucedido, basta verificar se os gastos com ele se limitaram ao orçamento planejado.
Para auxiliar na formatação de dados, o Flex 3 oferece algumas tags de formatação
pré estabelecidas. Assinale a alternativa que NÃO APRESENTA uma dessas tags:
Compare os dois trechos de código a seguir e assinale a alternativa correta:
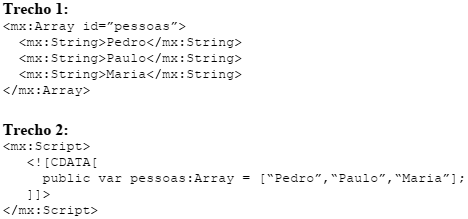
Analise o seguinte trecho de código em MXML e em seguida assinale a alternativa
correta:
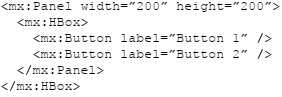
Ao tentar executar o código acima:
Atenção: A questão se refere ao seguinte texto:
Many businesses believe that if they purchase enough equipment, they can create a secure infrastructure. Firewalls, intrusion detection systems and antivirus programs are just some of the tools available to assist in protecting a network and its data. It is important to keep in mind that no product or combination of products will create a secure organization by itself. Security is a process; there is no tool that you can “set and forget”. All security products are only as secure as the people who configure and maintain them. The purchasing and implementation of security products should be only a percentage of the security budget. The employees tasked with maintaining the security devices should be provided with enough time, training, and equipment to properly support the products. Unfortunately, in many organizations security activities are less important than support activities. Highly skilled security professionals are often tasked with help-desk projects such as resetting forgotten passwords, fixing jammed printers, and setting up new employee workstations. For most organizations, the cost of creating a strong security posture is seen as a necessary evil, similar to purchasing insurance. Organizations don’t want to spend the money on it, but the risks of not making the purchase outweigh the costs. Because of this attitude, it is extremely challenging to create a secure organization. The attitude is enforced because requests for security tools are often supported by documents providing the average cost of a security incident instead of showing more concrete benefits of a strong security posture. The problem is exacerbated by the fact that IT professionals speak a different language than management. IT professionals are generally focused on technology. Management is focused on revenue. Concepts such as profitability, asset depreciation, return on investment, and total cost of ownership are the mainstays of management. These are alien concepts to most IT professionals.
Adaptado de: VACCA, John R. Computer and Information Security Handbook. Pg 5.
Atenção: A questão se refere ao seguinte texto:
Many businesses believe that if they purchase enough equipment, they can create a secure infrastructure. Firewalls, intrusion detection systems and antivirus programs are just some of the tools available to assist in protecting a network and its data. It is important to keep in mind that no product or combination of products will create a secure organization by itself. Security is a process; there is no tool that you can “set and forget”. All security products are only as secure as the people who configure and maintain them. The purchasing and implementation of security products should be only a percentage of the security budget. The employees tasked with maintaining the security devices should be provided with enough time, training, and equipment to properly support the products. Unfortunately, in many organizations security activities are less important than support activities. Highly skilled security professionals are often tasked with help-desk projects such as resetting forgotten passwords, fixing jammed printers, and setting up new employee workstations. For most organizations, the cost of creating a strong security posture is seen as a necessary evil, similar to purchasing insurance. Organizations don’t want to spend the money on it, but the risks of not making the purchase outweigh the costs. Because of this attitude, it is extremely challenging to create a secure organization. The attitude is enforced because requests for security tools are often supported by documents providing the average cost of a security incident instead of showing more concrete benefits of a strong security posture. The problem is exacerbated by the fact that IT professionals speak a different language than management. IT professionals are generally focused on technology. Management is focused on revenue. Concepts such as profitability, asset depreciation, return on investment, and total cost of ownership are the mainstays of management. These are alien concepts to most IT professionals.
Adaptado de: VACCA, John R. Computer and Information Security Handbook. Pg 5.