Questões de Concurso
Comentadas para cespe / cebraspe
Foram encontradas 49.625 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Julgue o próximo item, relativos às metodologias Scrum e XP e à biblioteca ITIL v4.
Enquanto a metodologia Scrum traz uma abordagem mais
voltada para a gestão, com maior foco nas reuniões, no
planejamento e na melhoria contínua, a metodologia XP tem
maior enfoque nas práticas técnicas.
Quanto ao OWASP Top 10, julgue o item seguinte.
Quando os desenvolvedores de software não testam a
compatibilidade de bibliotecas atualizadas ou corrigidas, isso
caracteriza um problema de segurança que o OWASP
nomeia como componentes vulneráveis e desatualizados.
ID Token é um artefato que carrega informações pessoais sobre os usuários finais, os quais se autenticam em um fluxo Open ID Connect.
A política de segurança da informação deve estar disponível como referência aberta para consulta fora da organização.
A política de segurança da informação somente deve ser comunicada dentro da organização quando for apropriado.
Acerca de conceitos relacionados a controle de acesso, julgue o item a seguir.
O uso de processos e ferramentas para criar, atribuir,
gerenciar e revogar credenciais de acesso para usuários é
considerado uma boa prática de segurança da informação.
Acerca de conceitos relacionados a controle de acesso, julgue o item a seguir.
Em situações de gerenciamento de acesso de usuários a
sistemas críticos, o uso de ferramentas de segundo fator de
autenticação e gerenciamento de acesso privilegiado é
restrito aos administradores do sistema.
A confidencialidade é uma propriedade segundo a qual as informações não podem ser disponibilizadas a indivíduos, entidades ou processos que não estejam previamente autorizados.
A integridade é uma propriedade que visa aplicar conhecimentos e habilidades para garantir a assinatura digital.
Tendo como referência as proposições P1 a P6, anteriormente apresentadas, julgue o item a seguir.
É válido o argumento que toma por premissas as proposições
P1 a P6 e, por conclusão, a proposição “esqueceu-se de
colocar seu nome na prova”.
Tendo como referência as proposições P1 a P6, anteriormente apresentadas, julgue o item a seguir.
A negação da proposição P6 pode ser corretamente expressa
por “a assinatura do aluno não consta da lista de presença do
dia da prova, mas o aluno não deixou de fazer a prova”.
Tendo como referência as proposições P1 a P6, anteriormente apresentadas, julgue o item a seguir.
É válido o argumento que toma por premissas as proposições
P1 a P6 e, por conclusão, a proposição “Se o aluno fez a
prova, então o professor perdeu a prova dele”.
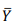 = (Y1+ Y2+…+ Y16)/16, julgue o próximo item.
= (Y1+ Y2+…+ Y16)/16, julgue o próximo item. A variável aleatória
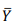 × 16 segue uma distribuição binomial
com parâmetro n = 16.
× 16 segue uma distribuição binomial
com parâmetro n = 16. 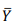 = (Y1+ Y2+…+ Y16)/16, julgue o próximo item.
= (Y1+ Y2+…+ Y16)/16, julgue o próximo item. O desvio padrão de
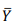 é igual a 32.
é igual a 32. The adjective “dull”, in the first sentence of the fourth paragraph, could be replaced by boring without changing the meaning of the sentence.
This is an informative text which mingles formal and colloquial vocabulary, such as “street cred”.
The advent of digital computers marked the moment when women were dismissed from calculation and coding.
The main point of the article is the ironic dismissal of women’s abilities to work in programming in disregard for their fundamental contribution to this area.
Tracy Chou, as a recognized programmer, is an exception since she has not suffered prejudice for being a woman during her career.
The terms data art and digital art are interchangeable in the text.