Questões de Concurso
Comentadas para fumarc
Foram encontradas 4.930 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Analise as afirmativas a seguir referentes à sintaxe da biblioteca jQuery:
I – O código “$("p").hide()” permite esconder todos os elementos “<p>”.
II – O código “$(".teste").hide()” permite esconder todos os elementos com o atributo id=“teste”.
III – O código “$("#teste").hide()” permite esconder todos os elementos com o atributo class=“teste”.
Está CORRETO apenas o que se afirma em:
Analise as afirmativas a seguir referentes ao formato JSON:
I – JSON é um acrônimo de JavaScript Object Notation.
II – JSON é um formato para intercâmbio de dados.
III – Um objeto JSON começa com uma “{“ e termina com uma “}”.
Estão CORRETAS as afirmativas:
Em relação às etapas de teste de software, correlacione as colunas a seguir:
Etapa de teste
1.Teste de unidade
2.Teste de integração
3.Teste de validação
4.Teste de sistema
Objetivo
( ) Foca no projeto e construção da arquitetura de software, ao mesmo tempo em que se realizam testes para descobrir erros associados às interfaces.( ) Garante que o software satisfaz a todos os requisitos funcionais, comportamentais e de desempenho.
( ) Verifica se o software e todos os outros elementos se combinam corretamente e se a função/desempenho global é obtido.
( ) Foca em cada componente individualmente, garantindo que ele funcione adequadamente.
A sequência CORRETA, de cima para baixo, é:
Em relação aos conceitos de verificação e validação relacionados ao teste de software, correlacione as colunas a seguir:
Tarefa
1.Verificação
2.Validação
Característica
( ) Checar se o software atende a seus requisitos funcionais e não funcionais.
( ) Garantir que o software atenda às expectativas do cliente.
( ) “Estamos construindo o produto certo?”.
( ) “Estamos construindo o produto da maneira certa?”.
( ) Garantir que o software implementa corretamente uma função específica.
A sequência CORRETA, de cima para baixo, é:
Em relação ao processo de integração contínua de software, analise as seguintes afirmativas.
I. Um dos benefícios de se trabalhar com integração contínua é permitir que os problemas causados pelas interações entre diferentes desenvolvedores sejam detectados e reparados tão logo seja possível.
II. A integração contínua é uma boa estratégia para sistemas muito grandes, quando se leva muito tempo para que o sistema seja construído (build) e testado.
III. Na integração contínua, assim que o trabalho em uma tarefa é concluído, ele é integrado ao sistema como um todo e, após essa integração, todos os testes de unidade do sistema devem passar.
Estão CORRETAS as afirmativas:
Analise as afirmativas referentes às estruturas de dados básicas:
I – Uma lista linear é uma sequência de zero ou mais itens x1, x2, ..., xn, em que xi é de um determinado tipo e n representa o tamanho da lista linear.
II – Uma pilha é uma lista linear em que todas as inserções, retiradas e geralmente todos os acessos, são feitos em apenas um extremo da lista.
III – Uma fila é uma lista linear em que todas as inserções são realizadas em um extremo da lista e todos os acessos e retiradas são realizados no mesmo extremo da lista.
Estão CORRETAS as afirmativas:
Ten critical actions needed to address four major cybersecurity challenges:
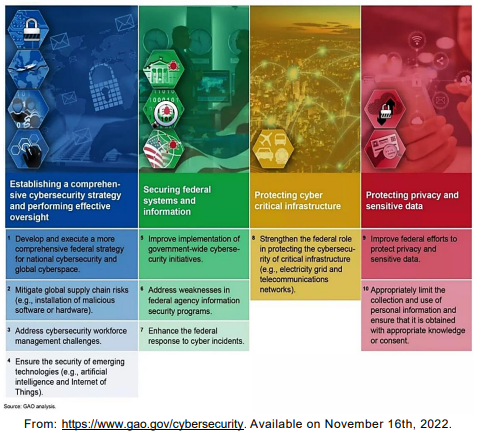
Ten critical actions needed to address four major cybersecurity challenges:

The use of the preposition for in “1. Develop and execute a more comprehensive
federal strategy for national cybersecurity…” indicates
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
According to the text, the escalating threats to IT systems
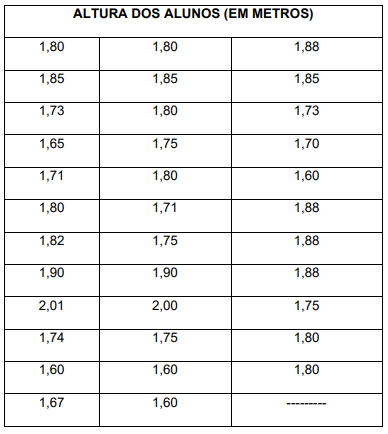
A altura mediana é igual a: