Questões de Concurso
Comentadas para analista de sistemas - desenvolvimento de sistemas
Foram encontradas 434 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Analise as afirmativas referentes às estruturas de dados básicas:
I – Uma lista linear é uma sequência de zero ou mais itens x1, x2, ..., xn, em que xi é de um determinado tipo e n representa o tamanho da lista linear.
II – Uma pilha é uma lista linear em que todas as inserções, retiradas e geralmente todos os acessos, são feitos em apenas um extremo da lista.
III – Uma fila é uma lista linear em que todas as inserções são realizadas em um extremo da lista e todos os acessos e retiradas são realizados no mesmo extremo da lista.
Estão CORRETAS as afirmativas:
Ten critical actions needed to address four major cybersecurity challenges:
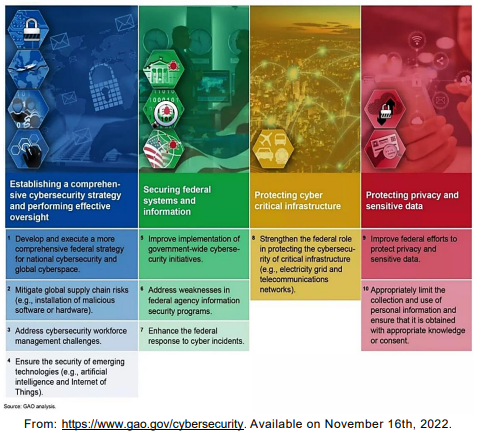
Ten critical actions needed to address four major cybersecurity challenges:

The use of the preposition for in “1. Develop and execute a more comprehensive
federal strategy for national cybersecurity…” indicates
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
According to the text, the escalating threats to IT systems
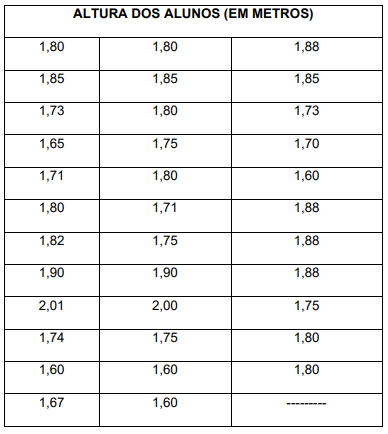
A altura mediana é igual a:
Para estruturar determinada armação de madeira em vigas de sustentação do telhado de um salão de jogos do clube, o planejamento foi desenhado previamente no seguinte projeto:
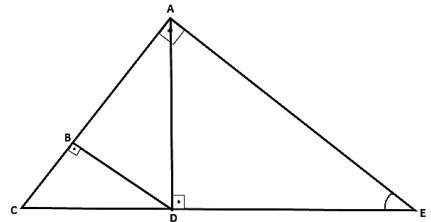
Considerando que o desenho acima está na escala 1:20 e que a medida CE, no
desenho, é igual a 80 cm e que o ângulo AÊD é igual a 30º , o comprimento BC de
madeira que deverá ser cortada para compor a estrutura deverá ser igual a
Julgue o item a seguir acerca de computação em nuvem.
Infrastructure as code (IaC) consiste na utilização de uma
linguagem de codificação descritiva de alto nível cujo
objetivo é automatizar o provisionamento da infraestrutura
de TI.