Questões de Concurso
Comentadas para programador de computador
Foram encontradas 2.803 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
I. int sum = 7; if ( sum > 20 ) {
System.out.print("ganhou "); } else {
System.out.print("perdeu "); } System.out.println("o bônus.");
II. int sum = 21; if ( sum != 20 )
System.out.print("ganhou"); else
System.out.print("perdeu "); System.out.println("o bônus.");
O resultado da execução dos fragmentos em I e II será, respectivamente,
Technology and legal pressure have changed
spammers’ terms of trade. They long relied on sending
more e-mails from more computers, knowing that some
will get through. But it is hard to send 100m e-mails
without someone noticing. In 2008 researchers from the
University of California at Berkeley and San Diego posed
as spammers, infiltrated a botnet and measured its
success rate. The investigation confirmed only 28 “sales”
on 350m e-mail messages sent, a conversion rate
under .00001%. Since then the numbers have got worse.
But spammers are a creative bunch.
 of tricking
of tricking consumers into a purchase, they are stealing their money
directly. Links used to direct the gullible to a site selling
counterfeits. Now they install “Trojan” software that
ransacks hard drives for bank details and the like.
Spammers also have become more sophisticated
about exploiting trust. In few places is it granted more
readily than on social-networking sites. Twitter, a forum for
short, telegram-like messages, estimates that only 1% of
its traffic is spam. But researchers from the University of
California at Berkeley and the University of Illinois at
Champaign-Urbana show that 8% of links published were
shady, with
 of them leading to scams and the rest to
of them leading to scams and the rest to Trojans. Links in Twitter messages, they found, are over
20 times more likely to get clicked than those in e-mail
spam.
Nor is Facebook as safe as it seems. As an
experiment, BitDefender, an online-security firm, set up
fake profiles on the social network and asked strangers to
enter into a digital friendship. They were able to create as
many as 100 new friends a day. Offering a profile picture,
particularly of a pretty woman, increased their odds. When
the firm’s researchers expanded their requests to strangers
who shared even one mutual friend, almost half accepted.
Worse, a quarter of BitDefender’s new friends clicked on
links posted by the firm, even when the destination was
obscured.
(Adapted from http://www.economist.com/node/17519964)
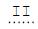 é
é Technology and legal pressure have changed
spammers’ terms of trade. They long relied on sending
more e-mails from more computers, knowing that some
will get through. But it is hard to send 100m e-mails
without someone noticing. In 2008 researchers from the
University of California at Berkeley and San Diego posed
as spammers, infiltrated a botnet and measured its
success rate. The investigation confirmed only 28 “sales”
on 350m e-mail messages sent, a conversion rate
under .00001%. Since then the numbers have got worse.
But spammers are a creative bunch.
 of tricking
of tricking consumers into a purchase, they are stealing their money
directly. Links used to direct the gullible to a site selling
counterfeits. Now they install “Trojan” software that
ransacks hard drives for bank details and the like.
Spammers also have become more sophisticated
about exploiting trust. In few places is it granted more
readily than on social-networking sites. Twitter, a forum for
short, telegram-like messages, estimates that only 1% of
its traffic is spam. But researchers from the University of
California at Berkeley and the University of Illinois at
Champaign-Urbana show that 8% of links published were
shady, with
 of them leading to scams and the rest to
of them leading to scams and the rest to Trojans. Links in Twitter messages, they found, are over
20 times more likely to get clicked than those in e-mail
spam.
Nor is Facebook as safe as it seems. As an
experiment, BitDefender, an online-security firm, set up
fake profiles on the social network and asked strangers to
enter into a digital friendship. They were able to create as
many as 100 new friends a day. Offering a profile picture,
particularly of a pretty woman, increased their odds. When
the firm’s researchers expanded their requests to strangers
who shared even one mutual friend, almost half accepted.
Worse, a quarter of BitDefender’s new friends clicked on
links posted by the firm, even when the destination was
obscured.
(Adapted from http://www.economist.com/node/17519964)
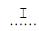 é
ésegurança, julgue os itens seguintes.
segurança, julgue os itens seguintes.
segurança, julgue os itens seguintes.
segurança, julgue os itens seguintes.
segurança, julgue os itens seguintes.
embasado em ciclos de vida executados em um arcabouço de
processos que empregam técnicas e ferramentas para transformar
entradas em saídas. Os processos são, ainda, agrupados quanto às
áreas de especialização e aos grupos. Com base nessas informações,
julgue os itens subsequentes.
embasado em ciclos de vida executados em um arcabouço de
processos que empregam técnicas e ferramentas para transformar
entradas em saídas. Os processos são, ainda, agrupados quanto às
áreas de especialização e aos grupos. Com base nessas informações,
julgue os itens subsequentes.
embasado em ciclos de vida executados em um arcabouço de
processos que empregam técnicas e ferramentas para transformar
entradas em saídas. Os processos são, ainda, agrupados quanto às
áreas de especialização e aos grupos. Com base nessas informações,
julgue os itens subsequentes.
embasado em ciclos de vida executados em um arcabouço de
processos que empregam técnicas e ferramentas para transformar
entradas em saídas. Os processos são, ainda, agrupados quanto às
áreas de especialização e aos grupos. Com base nessas informações,
julgue os itens subsequentes.
em sua estrutura, terminologia, processos e funções.