Questões de Concurso
Para analista de redes e comunicação de dados
Foram encontradas 1.919 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
Com base nas informações da situação hipotética acima descrita, julgue os itens a seguir.
Com base nas informações da situação hipotética acima descrita, julgue os itens a seguir.
verdadeira (V) ou falsa (F). As proposições são normalmente
representadas pelas letras maiúsculas A, B, C etc. A partir de
proposições dadas, podem-se construir novas proposições
compostas, mediante o emprego de símbolos lógicos chamados
conectivos: "e", indicado pelo símbolo lógico
 , e "ou", indicado pelo símbolo lógico
, e "ou", indicado pelo símbolo lógico  . Usa-se o modificador "não", representado pelo símbolo lógico ¬, para produzir a negação de uma
. Usa-se o modificador "não", representado pelo símbolo lógico ¬, para produzir a negação de umaproposição; pode-se, também, construir novas proposições
mediante o uso do condicional "se A então B", representado
por A
 B.O julgamento de uma proposição lógica composta
B.O julgamento de uma proposição lógica compostadepende do julgamento que se faz de suas proposições
componentes. Considerando os possíveis julgamentos V ou F das
proposições A e B, tem-se a seguinte tabela-verdade para
algumas proposições compostas.

Considerando-se a proposição A, formada a partir das
proposições B, C etc. mediante o emprego de conectivos (
 ou
ou ), ou de modificador (¬) ou de condicional (
), ou de modificador (¬) ou de condicional ( ), diz-se que A é uma tautologia quando A tem valor lógico V, dependentemente
), diz-se que A é uma tautologia quando A tem valor lógico V, dependentementedos valores lógicos de B, C etc. e diz-se que A é uma contradição
quando A tem valor lógico F, independentemente dos valores
lógicos de B, C etc. Uma proposição A é equivalente a uma
proposição B quando A e B têm as tabelas-verdade iguais, isto é,
A e B têm sempre o mesmo valor lógico.
 B)
B)  (¬A
(¬A 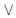 B) é uma tautologia.
B) é uma tautologia. 
Tomando por base o texto acima, julgue os itens de 9 a 15.

A partir do texto acima, julgue os itens de 1 a 8.

A partir do texto acima, julgue os itens de 1 a 8.