Questões de Concurso
Sobre interpretação de texto | reading comprehension em inglês
Foram encontradas 9.500 questões

The Office of Weights and Measures promotes uniformity in U.S. weights and measures laws, regulations, and standards to achieve equity between buyers and sellers in the marketplace. This enhances consumer confidence, enables U.S. businesses to compete fairly at home and abroad, and strengthens the U.S. economy.
OWM partners with the National Conference on Weights and Measures (NCWM), an organization of State and local weights and measures officials and representatives of business, industry, consumer groups, and Federal agencies, to develop U.S. standards in the form of uniform laws, regulations, and methods of practice. OWM serves as the U.S. representative to the International Organization of Legal Metrology (OIML) to bring efficiency and cost savings to U.S. manufacturers and other stakeholders doing business overseas, through the promotion of harmonized international standards and regulatory practices.
OWM ensures traceability of state weights and measures standards to the International System of Units (SI); develops procedures for legal metrology tests and inspections, and conducts training for laboratory metrologists and weights and measures officials. OWM provides guidance on the model weights and measures laws and regulations adopted by the NCWM and coordinates the development and publication of key NCWM publications.
It is estimated that sales of products or services impacted by weights and measures laws in the United States represent approximately 50 percent of the U.S. Gross Domestic Product. Industry sectors potentially affected by the decisions of the NCWM include retail food sales, other retail sales, petroleum products, transportation, and chemicals.
The NIST Office of Weights and Measures analyzes weights and measures training needs, obtains input from the weights and measures community, designs and delivers training for laboratory metrologists and weights and measures officials, measures the impact and effectiveness of training to ensure ongoing continual improvement, and consults with the weights and measures community to ensure ongoing professional development.
(Available in: http://www.nist.gov/pml/wmd.)
The Office of Weights and Measures promotes uniformity in U.S. weights and measures laws, regulations, and standards to achieve equity between buyers and sellers in the marketplace. This enhances consumer confidence, enables U.S. businesses to compete fairly at home and abroad, and strengthens the U.S. economy.
OWM partners with the National Conference on Weights and Measures (NCWM), an organization of State and local weights and measures officials and representatives of business, industry, consumer groups, and Federal agencies, to develop U.S. standards in the form of uniform laws, regulations, and methods of practice. OWM serves as the U.S. representative to the International Organization of Legal Metrology (OIML) to bring efficiency and cost savings to U.S. manufacturers and other stakeholders doing business overseas, through the promotion of harmonized international standards and regulatory practices.
OWM ensures traceability of state weights and measures standards to the International System of Units (SI); develops procedures for legal metrology tests and inspections, and conducts training for laboratory metrologists and weights and measures officials. OWM provides guidance on the model weights and measures laws and regulations adopted by the NCWM and coordinates the development and publication of key NCWM publications.
It is estimated that sales of products or services impacted by weights and measures laws in the United States represent approximately 50 percent of the U.S. Gross Domestic Product. Industry sectors potentially affected by the decisions of the NCWM include retail food sales, other retail sales, petroleum products, transportation, and chemicals.
The NIST Office of Weights and Measures analyzes weights and measures training needs, obtains input from the weights and measures community, designs and delivers training for laboratory metrologists and weights and measures officials, measures the impact and effectiveness of training to ensure ongoing continual improvement, and consults with the weights and measures community to ensure ongoing professional development.
(Available in: http://www.nist.gov/pml/wmd.)
E-mail Spoofing
E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source. Distributors of spam often use spoofing in an attempt to get recipients to open, and possibly even respond to, their solicitations. Spoofing can be used legitimately. However, spoofing anyone other than yourself is illegal in some jurisdictions.
E-mail spoofing is possible because Simple Mail Transfer Protocol (SMTP), the main protocol used in sending e-mail, does not include an authentication mechanism. Although an SMTP service extension (specified in IETF RFC 2554) allows an SMTP client to negotiate a security level with a mail
server, this precaution is not often taken. If the precaution is not taken, anyone with the requisite knowledge can connect to the server and use it to send messages. To send spoofed e-mail, senders insert commands in headers that will alter message information. It is possible to send a message that
appears to be from anyone, anywhere, saying whatever the sender wants it to say. Thus, someone could send spoofed e-mail that appears to be from you with a message that you didn't write.
Although most spoofed e-mail falls into the “nuisance" category and requires little action other than deletion, the more malicious varieties can cause serious problems and security risks. For example, spoofed e-mail may purport to be from someone in a position of authority, asking for sensitive data, such as passwords, credit card numbers, or other personal information – any of which can be used for a variety of criminal purposes. One type of e-mail spoofing, self- sending spam, involves messages that appear to be both to and from the recipient.
(http://searchsecurity.techtarget.com/definition/em.... Adaptado)
E-mail Spoofing
E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source. Distributors of spam often use spoofing in an attempt to get recipients to open, and possibly even respond to, their solicitations. Spoofing can be used legitimately. However, spoofing anyone other than yourself is illegal in some jurisdictions.
E-mail spoofing is possible because Simple Mail Transfer Protocol (SMTP), the main protocol used in sending e-mail, does not include an authentication mechanism. Although an SMTP service extension (specified in IETF RFC 2554) allows an SMTP client to negotiate a security level with a mail
server, this precaution is not often taken. If the precaution is not taken, anyone with the requisite knowledge can connect to the server and use it to send messages. To send spoofed e-mail, senders insert commands in headers that will alter message information. It is possible to send a message that
appears to be from anyone, anywhere, saying whatever the sender wants it to say. Thus, someone could send spoofed e-mail that appears to be from you with a message that you didn't write.
Although most spoofed e-mail falls into the “nuisance" category and requires little action other than deletion, the more malicious varieties can cause serious problems and security risks. For example, spoofed e-mail may purport to be from someone in a position of authority, asking for sensitive data, such as passwords, credit card numbers, or other personal information – any of which can be used for a variety of criminal purposes. One type of e-mail spoofing, self- sending spam, involves messages that appear to be both to and from the recipient.
(http://searchsecurity.techtarget.com/definition/em.... Adaptado)
E-mail Spoofing
E-mail spoofing is the forgery of an e-mail header so that the message appears to have originated from someone or somewhere other than the actual source. Distributors of spam often use spoofing in an attempt to get recipients to open, and possibly even respond to, their solicitations. Spoofing can be used legitimately. However, spoofing anyone other than yourself is illegal in some jurisdictions.
E-mail spoofing is possible because Simple Mail Transfer Protocol (SMTP), the main protocol used in sending e-mail, does not include an authentication mechanism. Although an SMTP service extension (specified in IETF RFC 2554) allows an SMTP client to negotiate a security level with a mail
server, this precaution is not often taken. If the precaution is not taken, anyone with the requisite knowledge can connect to the server and use it to send messages. To send spoofed e-mail, senders insert commands in headers that will alter message information. It is possible to send a message that
appears to be from anyone, anywhere, saying whatever the sender wants it to say. Thus, someone could send spoofed e-mail that appears to be from you with a message that you didn't write.
Although most spoofed e-mail falls into the “nuisance" category and requires little action other than deletion, the more malicious varieties can cause serious problems and security risks. For example, spoofed e-mail may purport to be from someone in a position of authority, asking for sensitive data, such as passwords, credit card numbers, or other personal information – any of which can be used for a variety of criminal purposes. One type of e-mail spoofing, self- sending spam, involves messages that appear to be both to and from the recipient.
(http://searchsecurity.techtarget.com/definition/em.... Adaptado)
Anonymous has named a man it claims posted topless pictures of a 15-year-old girl online and harassed her so relentlessly that she killed herself.
Amanda Todd, from Vancouver, Canada, was found hanged in her home on October 10, just weeks after she uploaded a video to YouTube detailing her horrific treatment at the hands of cyber bullies.
When she was just 12, a man in an internet chat room convinced her to flash her breasts, and a year later, he plastered a picture of the incident across Facebook.
Now in a vigilante move, Anonymous, the world's largest hacking group, has named the man allegedly responsible for the picture.
The group claims that he is a 32-year-old from British Columbia, but MailOnline has chosen not to identify him for legal reasons
As Todd's supporters set up Facebook pages warning the man to 'sleep with one eye open', the move by Anonymous sparks concerns over its abilities to create a 'trial by internet' - bypassing the justice system and casting guilt.
In a video posted to YouTube by Anonymous, a figure claims the group lists his personal information, including his date of birth and address
It explains that his username appears on websites where he 'blackmailed' and gave advice to young girls. The same username is also tied to a website with a 'jailbait' photo gallery. '[He] is an abomination to our society, and will be punished,' the Anonymous figure says.
Referring to the possibility they might have the wrong man, they add: 'At the most this is the person who did this to Amanda Todd, and at the least it's another pedophile that enjoys taking advantage of children.'
Following Anonymous' announcement, the web moved swiftly, with groups calling for his death and warning him to 'sleep with one eye open' cropping up on Facebook.
CKNW reporters have unsuccessfully tried to speak with the man, and neighbours have described his home as 'a known party house on the weekend with lots of young women coming and going'.
But police attended the home on Monday after a neighbour, Chyne Simpson, said Anonymous named the wrong address. He said he felt threatened by internet users and asked them to stay away.
The Royal Canadian Mounted Police refused to confirm Anonymous have the right man but a spokesperson said they were aware that someone had been named.
'We are aware of what's being posted online and certainly following up what we feel is important to follow up,' Sergeant Peter Thiessen told The Globe and Mail, adding: '[Vigilantes] run the risk of committing a criminal offence.'
Todd's family members also said they are not sure the Anonymous report is accurate and said police have tracked down a person living in the U.S. whom they believed was involved.
The claims come weeks after Amanda posted a nearly nine-minute YouTube video detailing her treatment on a stack of notecards held up to the camera.
Todd says that a year after she flashed her breasts, the man tracked her down and demanded he put on a show for him or he would expose her.
When she refused, he created a Facebook page with a list of her friends and used her naked chest as the profile photo. The picture quickly spread across the internet and among her classmates.
It led to relentless bullying online, she said, and she was diagnosed with depression and started drinking. In the video, posted September 7, she admitted that she had previously tried to kill herself twice and has been hospitalised.
After moving to a different city and school, another instance of bullying occurred after she started a romantic relationship with an older man who had a girlfriend. Once that relationship soured, she was confronted and beaten up by the man's girlfriend. She was hit in front of a crowd of screaming people who encouraged her to be left in a ditch.
Amanda does not speak in the video, and her face is not fully shown, but she confirmed her identity with the last notecard which says her name.
One of the final images is a jarring picture of her arm which had been cut repeatedly. Just under six weeks after posting the video, Todd could take the bullying no longer, and took her own life.
During a memorial for Todd on Monday, her friends said they have been aware of a man in his 30s 'stalking' their friend for years.
'There were multiple accounts with random names,' one friend told QMI Agency. 'There were Twitter accounts also used.' The Vancouver Sun reported that Amanda was a student in Grade 10 at the Coquitlam Basic Alternative Education school. The principal of the school confirmed her death and said that she had become connected with many since she transferred to the school in the middle of last year.
'It is a very sad case,' Paul McNaughton told the paper. 'I can tell you we feel we tried everything we could to help her when she came to us.'
Her death prompted a local politician to release a video of her own that pleads to put an end to bullying.
'I just heard about Amanda. I want to say to everyone who loved her, to all her family and friends, how sorry I am about her loss,' British Columbia premier Christy Clark said.
'No one deserves to be bullied. No one earns it. No one asks for it. It isn't a rite of passage. Bullying has to stop.'
http://www.dailymail.co.uk/news/article-2218532/Amanda-Todd-Anonymous-names-man-drove- teen-kill-spreading-nude-pictures.html
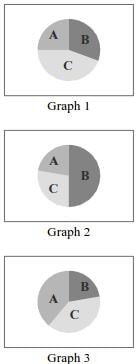
According to the data presented in lines 12 through 18 of the article, it is true that the secondary schools which have Wi-Fi in most or all classrooms are represented by






