Questões de Concurso
Sobre interpretação de texto | reading comprehension em inglês
Foram encontradas 9.532 questões
Ano: 2010
Banca:
ESAF
Órgão:
MPO
Prova:
ESAF - 2010 - MPOG - Analista de Planejamento e Orçamento - Prova 1 |
Q45356
Inglês
This text could best be characterized as
Q43729
Inglês
Texto associado
The Internet offers access to a wealth of material that is
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
children's relatives are supposed to judge whether the sites to be visited by their sons and daughters are proper for them to see.
Q43728
Inglês
Texto associado
The Internet offers access to a wealth of material that is
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
grown-up people are entitled to decide what choices to make as far as filtering is concerned.
Q43727
Inglês
Texto associado
The Internet offers access to a wealth of material that is
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
filtering software is used so as to make sure that improper sites won't be accessed.
Q43726
Inglês
Texto associado
The Internet offers access to a wealth of material that is
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
any individuals regardless of their ages can get into contact with valuable materials.
Q43725
Inglês
Texto associado
The Internet offers access to a wealth of material that is
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
personally, professionally and culturally enriching to individuals
of all ages. However, it also enables access to some material that
may be offensive, disturbing, illegal, inaccurate or incomplete.
Users are encouraged to evaluate the validity and appropriateness
of information accessed via the Internet.
Tests by the library and by independent agencies have shown that
filtering software may help to block access to objectionable
Internet sites. However, the software cannot block out all
objectionable sites, and it does sometimes block useful material,
including sites that are suitable for children, teens and adults.
Public Internet computers are equipped with commercial
filtering software. The library's filtering policy upholds the
principles of intellectual freedom, allowing adults to make their
own choices regarding filtering. The policy also aims to ensure
that our libraries are safe and welcoming places for children, and
it affirms the right and responsibility of parents to make choices
for their own children and teens.

According to the text above, it can be deduced that
through the Internet people can get information about wealthy materials.
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
SERPRO
Provas:
CESPE - 2008 - SERPRO - Analista - Desenvolvimento de Sistemas
|
CESPE - 2008 - SERPRO - Analista - Redes |
Q43308
Inglês
Texto associado
One frequently overlooked area in planning is technical
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
The plan is supposed to include the likelihood of failure, its results and the actions to be taken to contain development risk.
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
SERPRO
Provas:
CESPE - 2008 - SERPRO - Analista - Desenvolvimento de Sistemas
|
CESPE - 2008 - SERPRO - Analista - Redes |
Q43307
Inglês
Texto associado
One frequently overlooked area in planning is technical
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
In a lot of projects, it is hoped that the plan should be able to spot specific risky areas.
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
SERPRO
Provas:
CESPE - 2008 - SERPRO - Analista - Desenvolvimento de Sistemas
|
CESPE - 2008 - SERPRO - Analista - Redes |
Q43305
Inglês
Texto associado
One frequently overlooked area in planning is technical
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
Large projects demand patient learning to go through it.
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
SERPRO
Provas:
CESPE - 2008 - SERPRO - Analista - Desenvolvimento de Sistemas
|
CESPE - 2008 - SERPRO - Analista - Redes |
Q43304
Inglês
Texto associado
One frequently overlooked area in planning is technical
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
reviews and inspections. A technical review requires substantial
preparation on the part of the presenters. Documents must be
published and distributed and presentation material organized and
made into slides or overheads. Practice sessions are conducted by
presenters with an audience of critics to prepare for the review.
The reviewers should read the material, attend the
presentations, and write reports. On large projects with many
reviews and walk-throughs involving many participants, a
substantial number of labor hours can be consumed analyzing
documents, attending meetings, and writing reports. For example,
a system design review for one module or unit can require 150
labor hours. When overlooked, this labor can result in a very
large error in resource and schedule estimation.
Many projects include risk assessment and risk
management as a key part of the planning process and expect the
plan to identify specific risk areas. The plan is expected to
quantify both probability of failure and consequences of failure
and to describe what will be done to contain development risk.
A. Behforooz and F. Hudson. Software engineering
fundamentals. Ed. Oxford (adapted).
Based on the text above, judge the following items.
The reviewers must read and rewrite the material while being present in the meetings.
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42866
Inglês
Texto associado
Title:_____________
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
No texto, a expressão it would be years before the chip was even prototyped significa que
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42865
Inglês
Texto associado
Title:_____________
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
Segundo o autor do texto, a razão principal do fiasco do processador de Itanium deve-se a fato de
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42864
Inglês
Texto associado
Title:_____________
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
One could summarize the first paragraph by saying that the computer industry
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42863
Inglês
Texto associado
Title:_____________
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
January 26, 2009
By John C. Dvorak
It's no coincidence that the computer industry peaked around the year 2000, went into a serious decline, stabilized at the low point a couple of years ago, and has since collapsed again.
A confluence of reasons is responsible for this, but when it comes to the industry bringing this on itself, one major event may have taken down the entire business.
I'm speaking about the announcement of the Itanium processor. This continues to be one of the great fiascos of the last 50 years, and not because Intel blew too much money on its development or that the chip performed poorly and will never be widely adopted. It was the reaction and subsequent consolidation in the industry that took place once this grandiose chip was preannounced.
We heard that HP, IBM, Dell, and even Sun Microsystems would use these chips and discontinue anything else they were developing. This included Sun making noise about dropping the SPARC chip for this thing - sight unseen. I say "sight unseen" because it would be years before the chip was even prototyped. The entire industry just took Intel at its word that Itanium would work as advertised in a PowerPoint presentation.
Because this chip was supposed to radically change the way computers work and become the driving force behind all systems in the future, one promising project after another was dropped. Why? Because Itanium was the future for all computing. Why bother wasting money on good ideas that didn't include it?
The failure of this chip to do anything more than exist as a niche processor sealed the fate of Intel - and perhaps the entire industry, since from 1997 to 2001 everyone waited for the messiah of chips to take us all to the next level.
It did that all right. It took us to the next level. But we didn't know that the next level was below us, not above.
(Adapted from PCMAG.COM)
Um título adequado para o texto acima seria
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42862
Inglês
Texto associado
January 23, 2009
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the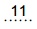 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the
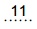 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Segundo o texto,
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42861
Inglês
Texto associado
January 23, 2009
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the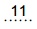 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the
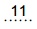 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
O Conficker, segundo o texto,
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42860
Inglês
Texto associado
January 23, 2009
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the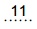 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the
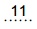 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Segundo o texto, sabe-se que o Conficker
Ano: 2009
Banca:
FCC
Órgão:
MPE-SE
Prova:
FCC - 2009 - MPE-SE - Analista do Ministério Público – Especialidade Análise de Sistemas |
Q42858
Inglês
Texto associado
January 23, 2009
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the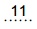 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
Worm Infects Millions of Computers Worldwide
By JOHN MARKOFF
A new digital plague has hit the Internet, infecting millions of personal and usiness computers in what seems to be the first step of a multistage attack. The world's eading computer security experts do not yet know who programmed the infection, or what the next stage will be.
In recent weeks a worm, a malicious software program, has swept through corporate, educational and public computer networks around the world. Known as Conficker or Downandup, it is spread by a recently discovered Microsoft Windows vulnerability, by guessing network passwords and by hand-carried consumer gadgets like USB keys.
Experts say it is the
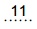 infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.
infection since the Slammer worm exploded through the Internet in January 2003, and it may have infected as many as nine million personal computers around the world.Worms like Conficker not only ricochet around the Internet at lightning speed, they harness infected computers into unified systems called botnets, which can then accept programming instructions from their clandestine masters.
Many computer users may not notice that their machines have been infected, and computer security researchers said they were waiting for the instructions to materialize, to determine what impact the botnet will have on PC users. It might operate in the background, using the infected computer to send spam or infect other computers, or it might steal the PC user's personal information.
Microsoft rushed an emergency patch to defend the Windows operating systems against this vulnerability in October, yet the worm has continued to spread even as the level of warnings has grown in recent weeks.
Earlier this week, security researchers at Qualys, a Silicon Valley security firm, estimated that about 30 percent of Windows-based computers attached to the Internet remain vulnerable to infection because they have not been updated with the patch, despite the fact that it was made available in October.
Unraveling the program has been particularly challenging because it comes with encryption mechanisms that hide its internal workings from those seeking to disable it.
The program uses an elaborate shell-game-style technique to permit someone to command it remotely. Each day it generates a new list of 250 domain names. Instructions from any one of these domain names would be obeyed. To control the botnet, an attacker would need only to register a single domain to send instructions to the botnet globally, greatly complicating the task of law enforcement and security companies trying to intervene and block the activation of the botnet.
Several computer security firms said that although Conficker appeared to have been written from scratch, it had parallels to the work of a suspected Eastern European criminal gang that has profited by sending programs known as "scareware" to personal computers that seem to warn users of an infection and ask for credit card numbers to pay for bogus antivirus software that actually further infects their computer.
One intriguing clue left by the malware authors is that the first version of the program checked to see if the computer had a Ukrainian keyboard layout. If it found it had such a keyboard, it would not infect the machine, according to Phillip Porras, a security investigator at SRI International who has disassembled the program to determine how it functioned.
(Adapted from The New York Times)
De acordo com o texto,
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
ABIN
Prova:
CESPE - 2008 - ABIN - Oficial de Inteligência |
Q42040
Inglês
Texto associado

Based on the text above, judge the following items.

Based on the text above, judge the following items.
Cocaine and military explosives remain for a longer time in one's finger tips.
Ano: 2008
Banca:
CESPE / CEBRASPE
Órgão:
ABIN
Prova:
CESPE - 2008 - ABIN - Oficial de Inteligência |
Q42039
Inglês
Texto associado

Based on the text above, judge the following items.

Based on the text above, judge the following items.
Cooks explained that, as cocaine and military explosives are likely to be difficult to be taken off, traces of them can be detected in a file or plastic binder if touched by someone who used them.
