O iptables pode ser utilizado para fazer o redirecio...
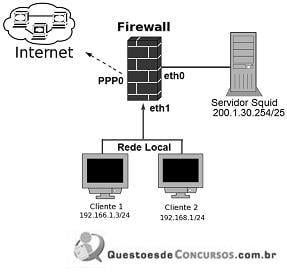
Com base na figura apresentada, assinale a alternativa que indica a regra iptables que possibilita o redirecionamento dos pacotes oriundos da Rede Local para o servidor Squid de IP 200.1.30.254, na sua porta padrão.
Gabarito comentado
Confira o gabarito comentado por um dos nossos professores
Clique para visualizar este gabarito
Visualize o gabarito desta questão clicando no botão abaixo
Comentários
Veja os comentários dos nossos alunos
Gabarito A
A única opção que contém a porta padrão 3128 do proxy Squid é a letra A, já que não é necessário utilizar o -j ACCEPT, que é o caso da letra E.
Vamos na fé !
"Retroceder Nunca Render-se Jamais !"
Força e Fé !
Fortuna Audaces Sequitur !
O Squid trabalha com os principais protocolos da Internet, alguns deles são: HTTP, HTTPS, FTP.
Ele também atua como Proxy transparente evitando que usuários "espertinhos" possam burlar o controle de acesso.
Http_port 3128: Define em qual porta o Squid vai atuar, a porta default é a 3128, mas podemos definir qualquer outra porta.
Com este conhecimento dava para matar a questão por eliminação, pois apenas a alternativa a apresenta a porta pad~roa do Squid 3128.
Fonte: https://www.vivaolinux.com.br/artigo/Servidor-proxy-com-Squid-Instalacao-e-configuracao
Com Jesus no barca as ondas não vão nos naufragar!
a-
Iptables is used to set up, maintain, and inspect the tables of IP packet filter rules in the Linux kernel. Several different tables may be defined. Each table contains a number of built-in chains and may also contain user-defined chains.
-t, --table table
This option specifies the packet matching table which the command should operate on. If the kernel is configured with automatic module loading, an attempt will be made to load the appropriate module for that table if it is not already there.
nat:
This table is consulted when a packet that creates a new connection is encountered. It consists of three built-ins: PREROUTING (for altering packets as soon as they come in), OUTPUT (for altering locally-generated packets before routing), and POSTROUTING (for altering packets as they are about to go out).
-A, --append chain rule-specification
Append one or more rules to the end of the selected chain. When the source and/or destination names resolve to more than one address, a rule will be added for each possible address combination.
-i, --in-interface [!] name
Name of an interface via which a packet was received (only for packets entering the INPUT, FORWARD and PREROUTING chains). When the "!" argument is used before the interface name, the sense is inverted. If the interface name ends in a "+", then any interface which begins with this name will match. If this option is omitted, any interface name will match.
-p, --protocol [!] protocol
The protocol of the rule or of the packet to check. The specified protocol can be one of tcp, udp, icmp, or all, or it can be a numeric value, representing one of these protocols or a different one.
-j, --jump target
This specifies the target of the rule; i.e., what to do if the packet matches it. The target can be a user-defined chain (other than the one this rule is in), one of the special builtin targets which decide the fate of the packet immediately, or an extension.
DNAT
This target is only valid in the nat table, in the PREROUTING and OUTPUT chains, and user-defined chains which are only called from those chains. It specifies that the destination address of the packet should be modified (and all future packets in this connection will also be mangled), and rules should cease being examined.
3128 - porta Squid
Clique para visualizar este comentário
Visualize os comentários desta questão clicando no botão abaixo