Questões de Concurso
Sobre inglês
Foram encontradas 18.859 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
English teaching methods and approaches
Throughout the history of teaching languages a number of different teaching approaches and methodologies have been tried and tested with some being more popular and effective than others. It’s beneficial to be familiar with a few of these.
1 – The Direct Method
The direct method of teaching English is also known as the Natural Method. It’s used to teach a number of different languages not just English, and the main idea of the Direct Method is that it only uses the target language that the students are trying to learn. Its main focus is oral skill and it is taught via repetitive drilling. Grammar is taught using an inductive way and students need to try and guess the rules through the teacher’s oral presentation.
2 – The Grammar Translation Method
This is the traditional or ‘classical’ way of learning a language and it’s still commonly used. Some countries prefer this style of teaching and the main idea behind this method is that the students learn all grammar rules, so they’re able to translate a number of sentences.
3 – The Audio Lingual Method
The Audio Lingual Method otherwise known as the New Key Method or Army Method is based on a behaviourist theory that things are able to be learned by constant reinforcement. This is related to the Direct Method and just like its predecessor it only uses the target language. The biggest difference between the Audio Lingual Method and the Direct Method is its focus of teaching. The Direct Methods focuses on the teaching of vocabulary whereas the Audio Lingual Method focuses on specific grammar teachings.
4 – The Structural Approach As the name suggests, the method is all about structure. The idea is that any language is made up of complex grammar rules. These rules, according to this approach need to be learnt in a specific order, for example the logical thing would be to teach the verb “to be” prior to teaching the present continuous which requires using the auxiliary form of the verb “to be”.
5 – Suggestopedia
This is a behaviourist theory and related to pseudoscience. This theory is intended to offer learners various choices. It relies a lot on the atmosphere and the physical surroundings of the class. It’s essential that all learners feel equally comfortable and confident. When teachers are training to use the Suggestopedia method, there’s a lot of art and music involved. Each Suggestopedia lesson is divided into three different phases – 1. Deciphering 2. Concert Session 3. Elaboration.
6 – Total Physical Response
Total Physical Response, otherwise known as TPR is an approach that follows the idea of ‘learning by doing’. Beginners will learn English through a series of repetitive actions such as “Stand up”, “Open your book”, “Close the door”, and “Walk to the window and open it.” With TPR, the most important skill is aural comprehension and everything else will follow naturally later.
7 – Communicative Language Teaching CLT
The idea behind this approach is to help learners communicate more effectively and correctly in realistic situations that they may find themselves in. This type of teaching involves focusing on important functions like suggesting, thanking, inviting, complaining, and asking for directions to name but a few.
8 – The Silent Way
The main of this way of teaching is for the teacher to say very little, so students can take control of their learning. There’s a big emphasis on pronunciation and a large chunk of the lesson focuses on it. This method of learning English follows a structural syllabus and grammar, vocabulary and pronunciation are constantly drilled and recycled for reinforcement. The teacher evaluates their students through careful observation, and it’s even possible that they may never set a formal test as learners are encouraged to correct their own language errors.
9 – Community Language Learning
This is probably one of the English teaching methods where the student feels the safest as there’s a great emphasis on the relationship and bond between the student and teacher. Unlike a lot of the other methods and approaches of teaching English as a Second Language, a lot of the L1 (mother tongue) is used for translation purposes.
10 – Task Based Language Learning
The main aim of this approach to learning is task completion. Usually, relevant and interesting tasks are set by the teacher and students are expected to draw on their pre-existing knowledge of English to complete the task with as few errors as possible.
11 – The Lexical Approach
The Lexical syllabus or approach is based on computer studies that have previously identified the most commonly used words. This approach in teaching focuses on vocabulary acquisition and teaching lexical chunks in order of their frequency and use. Teachers of the Lexical Approach place a great emphasis on authentic materials.
(Available: http://www.huntesl.com. Adapted.)
(Maya Angelou.) I’ve got the children to tend The clothes to mend The floor to mop The food to shop Then the chicken to fry The baby to dry I got company to feed The garden to weed I've got shirts to press The tots to dress The cane to be cut I gotta clean up this hut Then see about the sick And the cotton to pick. Shine on me, sunshine Rain on me, rain Fall softly, dewdrops And cool my brow again. Storm, blow me from here with your fiercest wind Let me float across the sky ‘til I can rest again, fall gently, snowflakes, Cover me with white cold icy kisses and let me rest tonight. Sun, rain, curving sky, mountain, oceans, leaf and stone You're all that I can call my own. (Available: http://www.aquaculturewithoutfrontiers.org.)
In “Fall softly, dewdrops” and “Let me float across the sky ‘til I can rest again, fall gently, snowflakes” the words GENTLY and SOFTLY convey the concept of:
The Story Behind TIME’s ‘Resilience of Ukraine’ Cover

(Artwork by JR; Photograph by Artem Iurchenko. A drone was used to capture the cover image on March 14 in Lviv.)
Since Russia’s invasion began, dozens of Ukraine’s 7.5 million children have been killed and thousands of others have fled in search of safety. Among those thousands is 5-year-old Valeriia from Kryvyi Rih, President Volodymyr Zelensky’s hometown in central Ukraine. Her image – a smiling child – appears on one of this issue’s covers.
If you met Valeriia, you might think she’s shy, her mother Taisiia told TIME, but don’t be fooled; at home, she commands attention. She loves the same things as many little girls – her stuffed bunny; her Elsa doll fromCold Heart(which English speakers know as Frozen); and her pink backpack, which she had to leave behind as she ran off her country. Valeriia also has big dreams: in particular, starting her first year of school on Sept. 1. Now, it’s hard to say when and where Valeriia will be able to do so. On March 9, mother and daughter fled to Poland; for safety, they asked that TIME use only their first names. In an interview, Taisiia explained her decision to leave home to keep her child safe. “She is my sunshine, my joy.”
According to Taisiia they woke up early in the morning of Feb. 24 to learn the occupying army had started bombing military bases. “I thought about my daughter, Valeriia; for her safety, I knew we had to go. We left Ukraine before we were bombarded, so we had a chance.” Even though Valeriia is with her now, husband and son stayed in Ukraine and therefore, it was very hard to leave. The day they left, the lines for buses and trainsstretched 3 km, mostly women and children, she says, “We were packed together and had to stand for 18 hours on the train to Lviv”.
The Russians still haven’t come to their city. The people from Kryvyi Rih have fought them off. But they are closer and closer, and you can see them approaching. In the media, Russia says they aren’t at war in Ukraine. But the war is real. People are dying for real. “And here I am, with my sister, my nephew, and my mother in Poland, in a hotel near Warsaw. They take care of us and even in this difficult situation, it was a warm reception. I cannot find the words to express how grateful I am to everyone who has helped”, ends up a crying Taisiia.
(Available: https://time.com/magazine/europe. Adapted.)
The Story Behind TIME’s ‘Resilience of Ukraine’ Cover

(Artwork by JR; Photograph by Artem Iurchenko. A drone was used to capture the cover image on March 14 in Lviv.)
Since Russia’s invasion began, dozens of Ukraine’s 7.5 million children have been killed and thousands of others have fled in search of safety. Among those thousands is 5-year-old Valeriia from Kryvyi Rih, President Volodymyr Zelensky’s hometown in central Ukraine. Her image – a smiling child – appears on one of this issue’s covers.
If you met Valeriia, you might think she’s shy, her mother Taisiia told TIME, but don’t be fooled; at home, she commands attention. She loves the same things as many little girls – her stuffed bunny; her Elsa doll fromCold Heart(which English speakers know as Frozen); and her pink backpack, which she had to leave behind as she ran off her country. Valeriia also has big dreams: in particular, starting her first year of school on Sept. 1. Now, it’s hard to say when and where Valeriia will be able to do so. On March 9, mother and daughter fled to Poland; for safety, they asked that TIME use only their first names. In an interview, Taisiia explained her decision to leave home to keep her child safe. “She is my sunshine, my joy.”
According to Taisiia they woke up early in the morning of Feb. 24 to learn the occupying army had started bombing military bases. “I thought about my daughter, Valeriia; for her safety, I knew we had to go. We left Ukraine before we were bombarded, so we had a chance.” Even though Valeriia is with her now, husband and son stayed in Ukraine and therefore, it was very hard to leave. The day they left, the lines for buses and trainsstretched 3 km, mostly women and children, she says, “We were packed together and had to stand for 18 hours on the train to Lviv”.
The Russians still haven’t come to their city. The people from Kryvyi Rih have fought them off. But they are closer and closer, and you can see them approaching. In the media, Russia says they aren’t at war in Ukraine. But the war is real. People are dying for real. “And here I am, with my sister, my nephew, and my mother in Poland, in a hotel near Warsaw. They take care of us and even in this difficult situation, it was a warm reception. I cannot find the words to express how grateful I am to everyone who has helped”, ends up a crying Taisiia.
(Available: https://time.com/magazine/europe. Adapted.)
Jane! I shouted... Where are you dear?
I am here, near the gas station… she replied.
The verbs “shouted” and “replied” underlined in the text refer to:
Complete the sentence with the correct form of the verb.
I always ________________ tired in the morning.
Ten critical actions needed to address four major cybersecurity challenges:
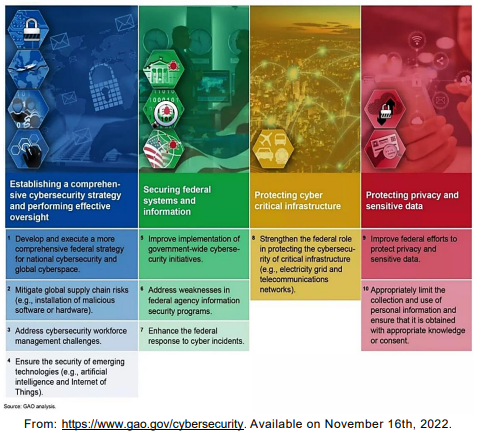
Ten critical actions needed to address four major cybersecurity challenges:

The use of the preposition for in “1. Develop and execute a more comprehensive
federal strategy for national cybersecurity…” indicates
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
What is the best alternative to fill the gaps to complete this conditional sentence?
“Until cybersecurity shortcoming ______ addressed, federal and critical infrastructure IT systems _______ increasingly susceptible to cyber threats.”
What is the BEST alternative to fill the gaps to complete this conditional sentence?
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
According to the text, the escalating threats to IT systems
Social media influencers
It is estimated that about 40 per cent of the world’s population use social media, and many of these billions of social media users look up to influencers to help them decide what to buy and what trends to follow.
So what is an influencer and how do we become one?
An influencer is a person who can influence the decisions of their followers because of their relationship with their audience and their knowledge and expertise in a particular area, e.g. fashion, travel or technology.
Influencers often have a large following of people who pay close attention to their views. They have the power to persuade people to buy things, and influencers are now seen by many companies as a direct way to customers’ hearts. Brands are now asking powerful influencers to market their products. With some influencers charging up to $25,000 for one social media post, it is no surprise that more and more people are keen to become influencers too. If you are one of them, then here are five tips on how to do it.
1. Choose your niche
What is the area that you know most about? What do you feel most excited talking about? Find the specific area that you’re most interested in and develop it.
2. Choose your medium and write an interesting bio
Most influencers these days are bloggers and micro-bloggers. Decide which medium – such as your own online blog, Instagram or Snapchat – is the best way to connect with your followers and chat about your niche area. When you have done that, write an attention-grabbing bio that describes you and your speciality area in an interesting and unique way. Make sure that people who read your bio will want to follow you.
3. Post regularly and consistently
Many influencers post daily on their social media accounts. The more you post, the more likely people will follow you. Also, ensure that your posts are consistent and possibly follow a theme.
4. Tell an interesting story
Whether it is a photo or a comment that you are posting, use it to tell a story that will catch the attention of your followers and help them connect with you.
5. Make sure people can easily find your content
Publicise your posts on a variety of social media, use hashtags and catchy titles and make sure that they can be easily found. There is no point writing the most exciting blogposts or posting the most attractive photographs if no one is going to see them.
Most importantly, if you want to become a social media influencer, you need to have patience. Keep posting and your following will gradually increase. Good luck!
Fonte: https://learnenglish.britishcouncil.org/skills/reading/b1-reading/social-media-influencers (Acesso em 17/10/2022
às 13h20)
Social media influencers
It is estimated that about 40 per cent of the world’s population use social media, and many of these billions of social media users look up to influencers to help them decide what to buy and what trends to follow.
So what is an influencer and how do we become one?
An influencer is a person who can influence the decisions of their followers because of their relationship with their audience and their knowledge and expertise in a particular area, e.g. fashion, travel or technology.
Influencers often have a large following of people who pay close attention to their views. They have the power to persuade people to buy things, and influencers are now seen by many companies as a direct way to customers’ hearts. Brands are now asking powerful influencers to market their products. With some influencers charging up to $25,000 for one social media post, it is no surprise that more and more people are keen to become influencers too. If you are one of them, then here are five tips on how to do it.
1. Choose your niche
What is the area that you know most about? What do you feel most excited talking about? Find the specific area that you’re most interested in and develop it.
2. Choose your medium and write an interesting bio
Most influencers these days are bloggers and micro-bloggers. Decide which medium – such as your own online blog, Instagram or Snapchat – is the best way to connect with your followers and chat about your niche area. When you have done that, write an attention-grabbing bio that describes you and your speciality area in an interesting and unique way. Make sure that people who read your bio will want to follow you.
3. Post regularly and consistently
Many influencers post daily on their social media accounts. The more you post, the more likely people will follow you. Also, ensure that your posts are consistent and possibly follow a theme.
4. Tell an interesting story
Whether it is a photo or a comment that you are posting, use it to tell a story that will catch the attention of your followers and help them connect with you.
5. Make sure people can easily find your content
Publicise your posts on a variety of social media, use hashtags and catchy titles and make sure that they can be easily found. There is no point writing the most exciting blogposts or posting the most attractive photographs if no one is going to see them.
Most importantly, if you want to become a social media influencer, you need to have patience. Keep posting and your following will gradually increase. Good luck!
Fonte: https://learnenglish.britishcouncil.org/skills/reading/b1-reading/social-media-influencers (Acesso em 17/10/2022
às 13h20)
1. An influencer has to know about a specific topic. 2. Influencers pay up to $25.000,00 to post about a company’s product. 3. An influencer should have a random bio.
Social media influencers
It is estimated that about 40 per cent of the world’s population use social media, and many of these billions of social media users look up to influencers to help them decide what to buy and what trends to follow.
So what is an influencer and how do we become one?
An influencer is a person who can influence the decisions of their followers because of their relationship with their audience and their knowledge and expertise in a particular area, e.g. fashion, travel or technology.
Influencers often have a large following of people who pay close attention to their views. They have the power to persuade people to buy things, and influencers are now seen by many companies as a direct way to customers’ hearts. Brands are now asking powerful influencers to market their products. With some influencers charging up to $25,000 for one social media post, it is no surprise that more and more people are keen to become influencers too. If you are one of them, then here are five tips on how to do it.
1. Choose your niche
What is the area that you know most about? What do you feel most excited talking about? Find the specific area that you’re most interested in and develop it.
2. Choose your medium and write an interesting bio
Most influencers these days are bloggers and micro-bloggers. Decide which medium – such as your own online blog, Instagram or Snapchat – is the best way to connect with your followers and chat about your niche area. When you have done that, write an attention-grabbing bio that describes you and your speciality area in an interesting and unique way. Make sure that people who read your bio will want to follow you.
3. Post regularly and consistently
Many influencers post daily on their social media accounts. The more you post, the more likely people will follow you. Also, ensure that your posts are consistent and possibly follow a theme.
4. Tell an interesting story
Whether it is a photo or a comment that you are posting, use it to tell a story that will catch the attention of your followers and help them connect with you.
5. Make sure people can easily find your content
Publicise your posts on a variety of social media, use hashtags and catchy titles and make sure that they can be easily found. There is no point writing the most exciting blogposts or posting the most attractive photographs if no one is going to see them.
Most importantly, if you want to become a social media influencer, you need to have patience. Keep posting and your following will gradually increase. Good luck!
Fonte: https://learnenglish.britishcouncil.org/skills/reading/b1-reading/social-media-influencers (Acesso em 17/10/2022
às 13h20)
Social media influencers
It is estimated that about 40 per cent of the world’s population use social media, and many of these billions of social media users look up to influencers to help them decide what to buy and what trends to follow.
So what is an influencer and how do we become one?
An influencer is a person who can influence the decisions of their followers because of their relationship with their audience and their knowledge and expertise in a particular area, e.g. fashion, travel or technology.
Influencers often have a large following of people who pay close attention to their views. They have the power to persuade people to buy things, and influencers are now seen by many companies as a direct way to customers’ hearts. Brands are now asking powerful influencers to market their products. With some influencers charging up to $25,000 for one social media post, it is no surprise that more and more people are keen to become influencers too. If you are one of them, then here are five tips on how to do it.
1. Choose your niche
What is the area that you know most about? What do you feel most excited talking about? Find the specific area that you’re most interested in and develop it.
2. Choose your medium and write an interesting bio
Most influencers these days are bloggers and micro-bloggers. Decide which medium – such as your own online blog, Instagram or Snapchat – is the best way to connect with your followers and chat about your niche area. When you have done that, write an attention-grabbing bio that describes you and your speciality area in an interesting and unique way. Make sure that people who read your bio will want to follow you.
3. Post regularly and consistently
Many influencers post daily on their social media accounts. The more you post, the more likely people will follow you. Also, ensure that your posts are consistent and possibly follow a theme.
4. Tell an interesting story
Whether it is a photo or a comment that you are posting, use it to tell a story that will catch the attention of your followers and help them connect with you.
5. Make sure people can easily find your content
Publicise your posts on a variety of social media, use hashtags and catchy titles and make sure that they can be easily found. There is no point writing the most exciting blogposts or posting the most attractive photographs if no one is going to see them.
Most importantly, if you want to become a social media influencer, you need to have patience. Keep posting and your following will gradually increase. Good luck!
Fonte: https://learnenglish.britishcouncil.org/skills/reading/b1-reading/social-media-influencers (Acesso em 17/10/2022
às 13h20)