Questões de Concurso
Sobre inglês
Foram encontradas 17.407 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!

According to the text, the rise of world sugar prices in the late 1980s immediately brought about
a decrease in ethanol prices.

According to the text, the rise of world sugar prices in the late 1980s immediately brought about
more consumption of ethanol.

According to the text, the history of the ethanol program in Brazil shows that
this program seems to be an intelligent solution to deal with
market price crises.

According to the text, the history of the ethanol program in Brazil shows that
this program progressed without difficulty from the very
beginning.

According to the text, the history of the ethanol program in Brazil shows that
the combination of land and climate conditions was a key
factor in the production of ethanol.

According to the text, the history of the ethanol program in Brazil shows that
this program was a reaction to the oil shortage of 1975.
Ten critical actions needed to address four major cybersecurity challenges:
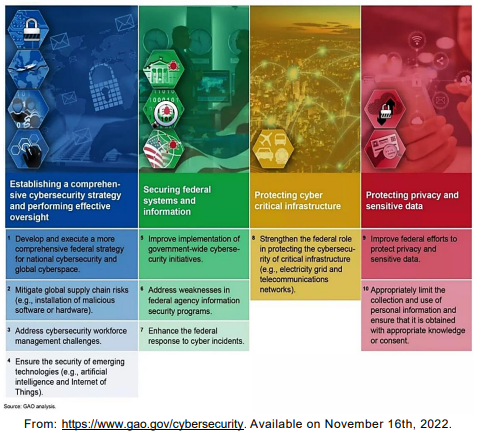
Ten critical actions needed to address four major cybersecurity challenges:

The use of the preposition for in “1. Develop and execute a more comprehensive
federal strategy for national cybersecurity…” indicates
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
Cybersecurity: An overview of cyber challenges facing the nation, and actions needed
Federal agencies and the nation’s critical infrastructure — such as energy, transportation systems, communications, and financial services — depend on Information Technology (IT) systems to carry out operations and process essential data. However, the risks to these IT systems are increasing—including insider threats from witting or unwitting employees, escalating and emerging threats from around the globe, and the emergence of new and more destructive attacks. Rapid developments in new technologies, such as artificial intelligence, the Internet of Things, and ubiquitous Internet and cellular connectivity, can also introduce security issues. Over 28,000 security incidents were reported by federal civilian agencies to the Department of Homeland Security in FY 2019.
Additionally, since many government IT systems contain vast amounts of personally identifiable information (PII), federal agencies must protect the confidentiality, integrity, and availability of this information—and effectively respond to data breaches and security incidents. Likewise, the trend in the private sector of collecting extensive and detailed information about individuals needs appropriate limits.
To highlight the importance of these issues, Government Accountability Office (GAO) has designated information security as a government-wide high-risk area since 1997. This high-risk area was expanded in 2003 to include the protection of critical cyber infrastructure and, in 2015, to include protecting the privacy of PII.
GAO has made about 3,300 recommendations to federal agencies to address cybersecurity shortcomings—and we reported that more than 750 of these had not been fully implemented as of December 2020. We designated 67 as priority, meaning that we believe they warrant priority attention from heads of key departments and agencies.
Adapted from: https://www.gao.gov/cybersecurity. Available on November 16th, 2022
According to the text, the escalating threats to IT systems
“Savings accounts are designed to hold money over a long period of time to help you save for larger goals (rather than everyday purchases). As your money stays in the account, it will accrue interest and grow over time. This means that you will need to visit your bank, set up a transfer online, or make an ATM withdrawal to access your money.”
I. While both allow you to access your money, you may consider it easier to do so with checking accounts (1st paragraph). II. In contrast, savings accounts have a limit on the number of withdrawals you can make each month (1st paragraph). III. Most banks won’t allow people under the age of 18 to open a checking account without a parent or legal guardian as a co-owner of the account (2nd paragraph). IV. When it comes to setting aside money for a long-term need or goal, you should consider a savings account (3rd paragraph). V. There are also dedicated savings accounts for kids, though a parent or guardian is usually required as a joint owner (4th paragraph).
Now, choose the alternative that classifies these terms correctly and matches them with an appropriate synonym.
Marque a alternativa CORRETA que substitui respectivamente o X e o Y no texto acima.
Read the sentences below.
I.The Novel was written by a Danish author.
II.The chest was full of flowers.
Considering the context of each sentence, mark the
alternative that presents the translation of the words
in bold.