Questões de Concurso Para tre-pr
Foram encontradas 955 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Considere que um Analista Judiciário é membro do Time Scrum e está participando de uma reunião de 4 horas, na qual ocorrem as atividades:
− O Product Owner esclarece quais itens do Backlog do Produto ficaram e quais não ficaram “Prontos”.
− O Time de Desenvolvimento discute o que foi bem, quais problemas ocorreram dentro da Sprint e como estes problemas foram resolvidos.
− O Time de Desenvolvimento demonstra o trabalho que está “Pronto” e responde as questões sobre o incremento.
− O Product Owner apresenta o Backlog do Produto tal como está e, se necessário, projeta as prováveis datas de conclusão baseado no progresso até a data.
− É feita uma análise da linha do tempo, orçamento, potenciais capacidades e mercado para a próxima versão esperada do produto.
O Analista está participando da Reunião
Consider the figure below showing a hypothetical situation. A criminal holds an hostage and against that, a cop (policeman) also holds an hostage who is a friend of the criminal. In this case, criminal is not going to let the hostage go if cop won't let his friend to let go. Also the cop is not going to let the friend of criminal let go, unless the criminal releases the hostage.
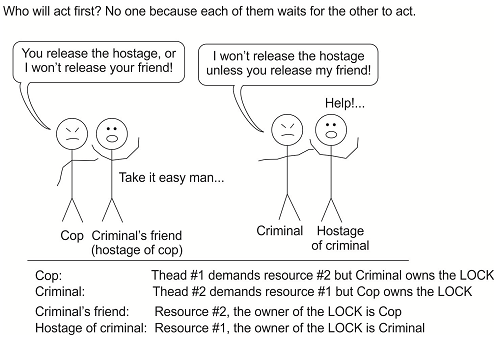
Analysing the situation from an Operational System´s point of view, a correct conclusion is
Considere o programa Java abaixo.

As lacunas de I a IV devem ser substituídas por expressões Java que completem adequadamente os comandos. Em
condições ideais, é correto afirmar que a lacuna
Consider the statements below.
I. It is defined as a procedure requiring the combination of several factors, including at least two of the following: Knowledge-something the user knows, e.g., a password, a personal identification number (PIN); Ownership-something the user has, e.g., token, smart card, mobile phone/SIM; Inherence − something the user is, e.g., fingerprint. It is worth highlighting that the aforementioned requirement of having mutually independent factors could be difficult to match. In fact, in the context of access to Internet services, when using ownership and inherence factors as well as when inputting a PIN or password, the user transmits digital data to the verifying counterpart, so that regardless of the generating factor, susceptibility to interception is a common vulnerability.
II. Security administration can be costly and prone to error because administrators usually specify access control lists for each user on the system individually. With this kind of control, security is managed at a level that corresponds closely to the organization's structure. Each user is assigned one or more roles, and each role is assigned one or more privileges that are permitted to users in that role. Security administration with it consists of determining the operations that must be executed by persons in particular jobs, and assigning employees to the proper roles. Complexities introduced by mutually exclusive roles or role hierarchies are handled by its software, making security administration easier.
The statements I and II refers respectively to