Questões de Concurso
Para tj-sc
Foram encontradas 1.760 questões
Resolva questões gratuitamente!
Junte-se a mais de 4 milhões de concurseiros!
Atenção: A questão se refere ao seguinte texto:
Many businesses believe that if they purchase enough equipment, they can create a secure infrastructure. Firewalls, intrusion detection systems and antivirus programs are just some of the tools available to assist in protecting a network and its data. It is important to keep in mind that no product or combination of products will create a secure organization by itself. Security is a process; there is no tool that you can “set and forget”. All security products are only as secure as the people who configure and maintain them. The purchasing and implementation of security products should be only a percentage of the security budget. The employees tasked with maintaining the security devices should be provided with enough time, training, and equipment to properly support the products. Unfortunately, in many organizations security activities are less important than support activities. Highly skilled security professionals are often tasked with help-desk projects such as resetting forgotten passwords, fixing jammed printers, and setting up new employee workstations. For most organizations, the cost of creating a strong security posture is seen as a necessary evil, similar to purchasing insurance. Organizations don’t want to spend the money on it, but the risks of not making the purchase outweigh the costs. Because of this attitude, it is extremely challenging to create a secure organization. The attitude is enforced because requests for security tools are often supported by documents providing the average cost of a security incident instead of showing more concrete benefits of a strong security posture. The problem is exacerbated by the fact that IT professionals speak a different language than management. IT professionals are generally focused on technology. Management is focused on revenue. Concepts such as profitability, asset depreciation, return on investment, and total cost of ownership are the mainstays of management. These are alien concepts to most IT professionals.
Adaptado de: VACCA, John R. Computer and Information Security Handbook. Pg 5.
Analise as afirmativas a seguir e assinale a alternativa correta, de acordo com as ideias apresentadas no texto:
I. Os funcionários encarregados de manter os dispositivos de segurança devem ser providos com tempo, treinamento e equipamentos suficientes para manter adequadamente os produtos.
II. A compra e implementação de produtos de segurança deve representar 100% do orçamento de segurança.
III. Em muitas organizações, as atividades de apoio são mais importantes do que as atividades de segurança.
Atenção: A questão se refere ao seguinte texto:
Many businesses believe that if they purchase enough equipment, they can create a secure infrastructure. Firewalls, intrusion detection systems and antivirus programs are just some of the tools available to assist in protecting a network and its data. It is important to keep in mind that no product or combination of products will create a secure organization by itself. Security is a process; there is no tool that you can “set and forget”. All security products are only as secure as the people who configure and maintain them. The purchasing and implementation of security products should be only a percentage of the security budget. The employees tasked with maintaining the security devices should be provided with enough time, training, and equipment to properly support the products. Unfortunately, in many organizations security activities are less important than support activities. Highly skilled security professionals are often tasked with help-desk projects such as resetting forgotten passwords, fixing jammed printers, and setting up new employee workstations. For most organizations, the cost of creating a strong security posture is seen as a necessary evil, similar to purchasing insurance. Organizations don’t want to spend the money on it, but the risks of not making the purchase outweigh the costs. Because of this attitude, it is extremely challenging to create a secure organization. The attitude is enforced because requests for security tools are often supported by documents providing the average cost of a security incident instead of showing more concrete benefits of a strong security posture. The problem is exacerbated by the fact that IT professionals speak a different language than management. IT professionals are generally focused on technology. Management is focused on revenue. Concepts such as profitability, asset depreciation, return on investment, and total cost of ownership are the mainstays of management. These are alien concepts to most IT professionals.
Adaptado de: VACCA, John R. Computer and Information Security Handbook. Pg 5.
Analise as afirmativas a seguir e assinale a alternativa correta, de acordo com as ideias apresentadas no texto:
I. Muitas empresas acreditam que não é necessário adquirir equipamentos para criar uma infraestrutura segura.
II. Firewalls, sistemas de detecção de intrusão e programa antivírus são apenas algumas das ferramentas disponíveis para ajudar a proteger uma rede e seus dados.
III. Nenhum produto ou combinação de produtos vai criar uma organização segura por si só.
IV. Para auxiliar na criação de um processo de segurança, existem ferramentas que você pode “configurar e esquecer”.
Atenção: A questão se refere ao seguinte texto:
What makes determining the causes of project failure so tough are all of the variables involved. Companies, teams, and projects have different sets of requirements and environmental factors that can influence outcome. Small and seemingly harmless circumstances can be like a "snowball" and bring the whole project to a standstill. "Project failure", however, is not synonymous with "project death". There are varying degrees of failure. The most extreme case, of course, is total project cancellation, and perhaps a few broken windows and bruised egos. But a project can also be considered a failure if it deviates too far from original specifications, doesn't meet key user requirements, and is late or over budget. The list of reasons for project failure is a long one, but we can conclude that the main causes are: setting an overly ambitious project scope, absence of project methodology, lack of support from senior management and poor interpersonal skills.
Adaptado de: CHIN, Paul. Cold Case File: Why Projects Fail. Revista IT Management, 06/05/2003.
Atenção: A questão se refere ao seguinte texto:
What makes determining the causes of project failure so tough are all of the variables involved. Companies, teams, and projects have different sets of requirements and environmental factors that can influence outcome. Small and seemingly harmless circumstances can be like a "snowball" and bring the whole project to a standstill. "Project failure", however, is not synonymous with "project death". There are varying degrees of failure. The most extreme case, of course, is total project cancellation, and perhaps a few broken windows and bruised egos. But a project can also be considered a failure if it deviates too far from original specifications, doesn't meet key user requirements, and is late or over budget. The list of reasons for project failure is a long one, but we can conclude that the main causes are: setting an overly ambitious project scope, absence of project methodology, lack of support from senior management and poor interpersonal skills.
Adaptado de: CHIN, Paul. Cold Case File: Why Projects Fail. Revista IT Management, 06/05/2003.
Atenção: A questão se refere ao seguinte texto:
What makes determining the causes of project failure so tough are all of the variables involved. Companies, teams, and projects have different sets of requirements and environmental factors that can influence outcome. Small and seemingly harmless circumstances can be like a "snowball" and bring the whole project to a standstill. "Project failure", however, is not synonymous with "project death". There are varying degrees of failure. The most extreme case, of course, is total project cancellation, and perhaps a few broken windows and bruised egos. But a project can also be considered a failure if it deviates too far from original specifications, doesn't meet key user requirements, and is late or over budget. The list of reasons for project failure is a long one, but we can conclude that the main causes are: setting an overly ambitious project scope, absence of project methodology, lack of support from senior management and poor interpersonal skills.
Adaptado de: CHIN, Paul. Cold Case File: Why Projects Fail. Revista IT Management, 06/05/2003.
Analise as afirmativas a seguir e assinale a alternativa correta, de acordo com o texto:
I. Os termos “falha do projeto” e “morte do projeto” podem ser considerados sinônimos.
II. Determinar as causas do fracasso de projetos é difícil por causa das janelas quebradas e egos machucados.
III. O caso mais extremo de falha é o cancelamento total do projeto.
Atenção: A questão se refere ao seguinte texto:
According a recent research, the Americans devote 22,7% of the time they spend on the Internet on social networking sites and blogs. A year ago, this number it was lower than 16%. Driving this trend is the social networking Facebook, which recently celebrated reaching half a billion users worldwide. It claimed an 85% share of social networking use; MySpace came in a distant second with a 5% share; and Twitter with just 1%. For the first time, games beat out e-mail as the No. 2 online time killer, accounting for 10% of time spent. The research found that half of all Americans online spend time playing games like online-gaming Zynga’s explosively popular FarmVille. It was unclear if time spent playing games like FarmVille on Facebook significantly influenced how much time people spend on Facebook. It’s not that people are not e-mailing or using instant messaging. They are engaged in those activities on services such as Facebook. And they are still heavily involved in those activities while online. E-mail was the third most popular activity at 8%, and instant messaging came in fifth at 4%. The other activity on the rise is watching videos and movies on YouTube, Hulu and Netflix, which jumped 12% to account for nearly 4% of all time spent online.
Adaptado de: GUYNN, Jessica. Social networking tops e-mail as most popular online activity. Los Angeles Times Website, 02/08/2010.
Atenção: A questão se refere ao seguinte texto:
According a recent research, the Americans devote 22,7% of the time they spend on the Internet on social networking sites and blogs. A year ago, this number it was lower than 16%. Driving this trend is the social networking Facebook, which recently celebrated reaching half a billion users worldwide. It claimed an 85% share of social networking use; MySpace came in a distant second with a 5% share; and Twitter with just 1%. For the first time, games beat out e-mail as the No. 2 online time killer, accounting for 10% of time spent. The research found that half of all Americans online spend time playing games like online-gaming Zynga’s explosively popular FarmVille. It was unclear if time spent playing games like FarmVille on Facebook significantly influenced how much time people spend on Facebook. It’s not that people are not e-mailing or using instant messaging. They are engaged in those activities on services such as Facebook. And they are still heavily involved in those activities while online. E-mail was the third most popular activity at 8%, and instant messaging came in fifth at 4%. The other activity on the rise is watching videos and movies on YouTube, Hulu and Netflix, which jumped 12% to account for nearly 4% of all time spent online.
Adaptado de: GUYNN, Jessica. Social networking tops e-mail as most popular online activity. Los Angeles Times Website, 02/08/2010.
Atenção: A questão se refere ao seguinte texto:
According a recent research, the Americans devote 22,7% of the time they spend on the Internet on social networking sites and blogs. A year ago, this number it was lower than 16%. Driving this trend is the social networking Facebook, which recently celebrated reaching half a billion users worldwide. It claimed an 85% share of social networking use; MySpace came in a distant second with a 5% share; and Twitter with just 1%. For the first time, games beat out e-mail as the No. 2 online time killer, accounting for 10% of time spent. The research found that half of all Americans online spend time playing games like online-gaming Zynga’s explosively popular FarmVille. It was unclear if time spent playing games like FarmVille on Facebook significantly influenced how much time people spend on Facebook. It’s not that people are not e-mailing or using instant messaging. They are engaged in those activities on services such as Facebook. And they are still heavily involved in those activities while online. E-mail was the third most popular activity at 8%, and instant messaging came in fifth at 4%. The other activity on the rise is watching videos and movies on YouTube, Hulu and Netflix, which jumped 12% to account for nearly 4% of all time spent online.
Adaptado de: GUYNN, Jessica. Social networking tops e-mail as most popular online activity. Los Angeles Times Website, 02/08/2010.
Analise as afirmativas a seguir e assinale a alternativa correta, de acordo com o texto:
I. Os sites de redes sociais e blogs são responsáveis por 22,7% do tempo que os americanos passam na Internet.
II. O Facebook atingiu recentemente a marca de meio bilhão de usuários somente nos Estados Unidos.
III. Os americanos dedicam 85% do tempo que passam na Internet usando o Facebook.
IV. O MySpace representa 5% do tempo que os americanos gastam com redes sociais.
O Brasil, pela sua extensão territorial, é considerado um país de grandes contrastes regionais.
A divisão do imenso território brasileiro em espaços geográficos regionais sempre constituiu um problema.
Em 1967, o IBGE ( Instituto Brasileiro de Geografia e Estatística ) adotou a atual divisão regional em 5 macro regiões, representadas no mapa abaixo.
Assinale as proposições em que as regiões delimitadas no mapa (A, B, C, D e E) estão corretamente caracterizadas.
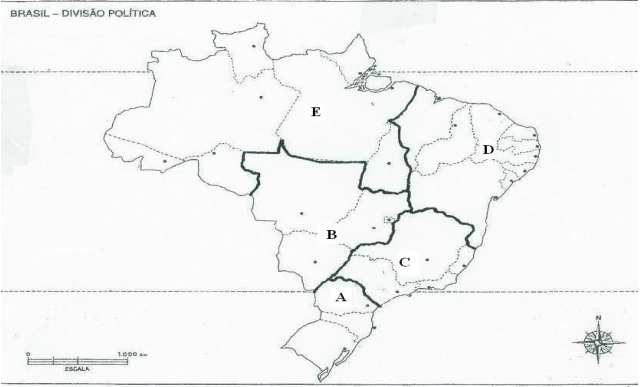
I. REGIÃO A: Apresenta aspectos naturais e sócios econômicos que caracterizam e diferenciam esta região das outras áreas do país. Os estados que a compõe estão entre as unidades da federação de melhor Índice de Desenvolvimento Humano ( IDH ) do Brasil.
II. REGIÃO B: Região de ocupação efetiva após 1960, quando apresentou um forte crescimento demográfico. A sua economia está relacionada ao agro-negócio; amplas áreas com o cultivo mecanizado de cereais para exportação.
III. REGIÃO C: Se caracteriza por ser a região econômica do país. Maior PIB (Produto Interno Bruto). Além do desenvolvimento econômico, esta região se destaca pela alta qualidade de vida. Estes destaques estão presentes em todos os estados da região, não existindo desigualdades econômicas e sociais entre eles.
IV. REGIÃO D: É considerada a região problema do Brasil, não devido às suas características climáticas mas, principalmente, injusta estrutura sócio-econômica da região, onde encontramos os Índices de Desenvolvimento Humano mais baixos do país.
V. REGIÃO E: Região natural por excelência. A sua ocupação recente se deu através das frentes pioneiras, incentivadas pelo governo federal, na década de 1970, para povoar novas regiões, como também, pelos grandes projetos mineralógicos e hidrelétricos desenvolvidos com a preocupação da preservação e do equilíbrio ambiental desta região.
Estão corretas as proposições: